Cloud-native SIEM
Detect and respond to threats at unparalleled scale
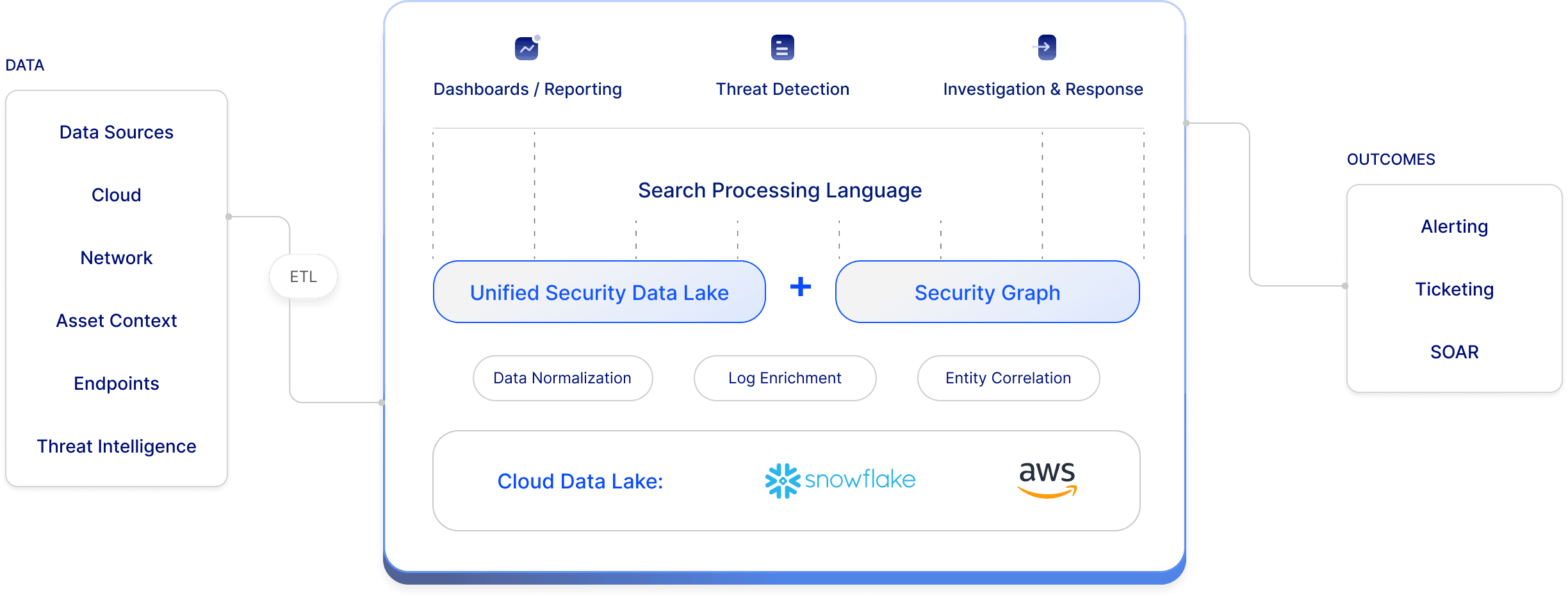
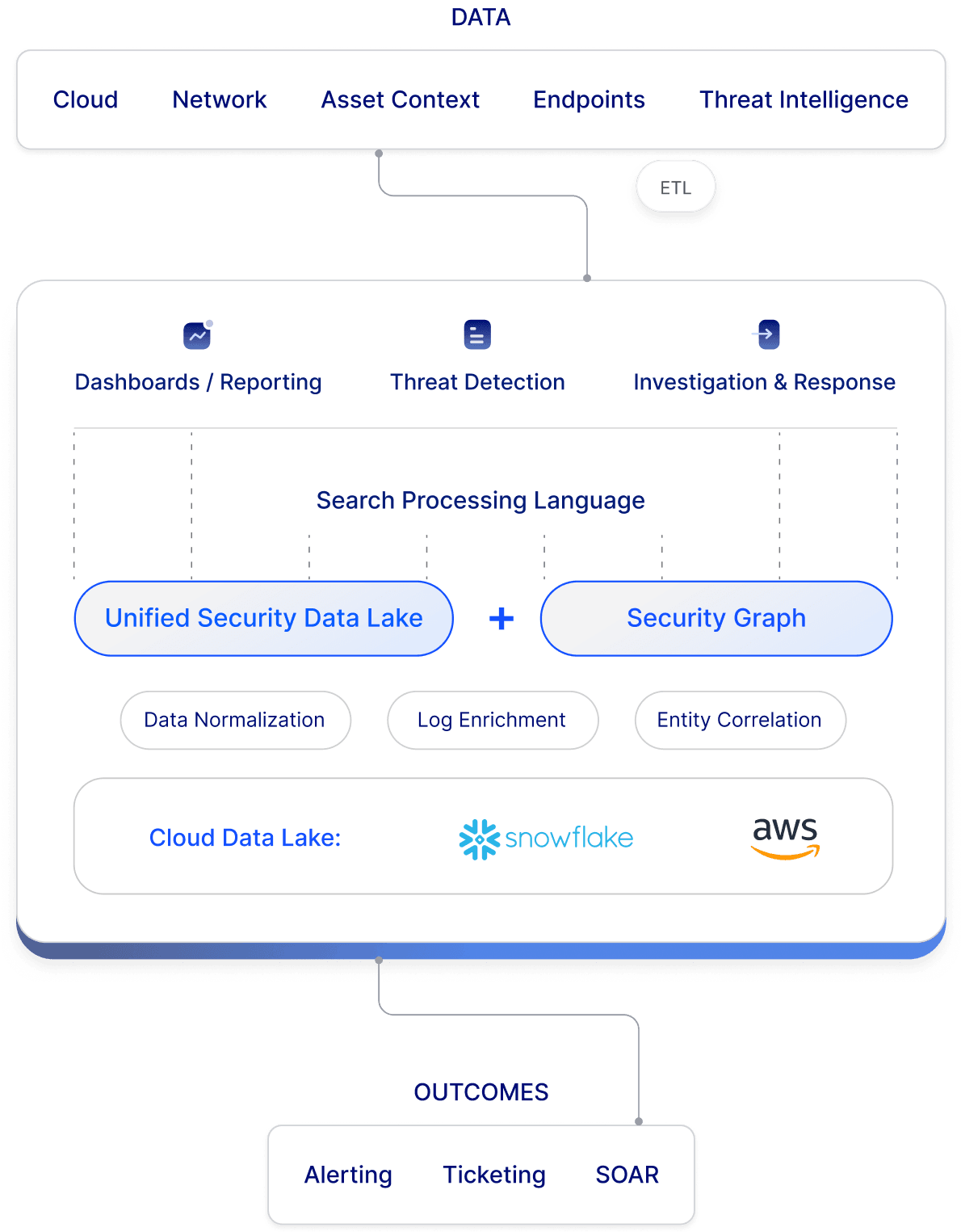
Reduce costs and help your existing team detect threats faster with Matano’s full-featured platform built on a security data lake. Simplify security operations with real-time threat detection, deep context, fast search, and unlimited data retention.
6x
reduction in total cost of ownership (TCO)
Cloud-native data lake scale on pure object storage with unlimited retention, and a predictable pricing model so you don’t have to compromise security visibility due to cost and scalability concerns.
1000+
pre-built parsers
Automatic integration with 1000+ data sources, normalized to a common schema (ECS) using pre-built parsers and enriched using context from threat intelligence feeds and the Security Graph.
800+
detection rules
Over 800 out-of-the-box detection rules, spanning your entire environment from endpoint and network to cloud, including correlation rules detecting threats across multiple data sources.
KEY FEATURES
Explore Matano SIEM
Respond proactively to security alerts, leveraging the tools that your teams are familiar with
Collect all your logs into a scalable data lake
Matano helps you ingest and normalize unstructured security logs into Snowflake and AWS for blazing fast search and analytics. Your data is always stored in S3 for unlimited retention at petabyte scale. Leverage hundreds of pre built connectors to ETL data from common security sources like Cloud, SaaS, Host, Network, and Identity logs.
Simplify data onboarding
Collect data at scale with built in data collection via APIs across applications, SaaS, and infrastructure, both on-premises and in multiple clouds. Configure new data sources within a few clicks, including data collection, parsing, correlations, dashboards and more.
Enrich, transform, and normalize security data
Normalize data into a common unified schema (ECS) spanning user, asset, IoC dimensions and other attributes. Enrich data in realtime with threat intelligence, geolocation, and custom sources. Use the lightweight VRL scripting language to extend built in parsers and apply custom transformations at ingest time.
Unlimited Data Retention, Unlimited Scale
Matano works on top of your S3 bucket and does not resell object storage. Cost-effectively scale to petabytes of data on object storage, and retain data long term for unlimited time periods. Keep ownership of your data in your cloud.
Search and detect using SPL compatible query language
Quickly search your data lake for IOC’s and pivot across hundreds of common fields using the Elastic Common Schema (ECS). Use Matano Query Language (with Splunk SPL compatibility) to slice and dice data into charts and visualizations for interactive threat hunts.
High fidelity customizable detection rules
Detect threats in realtime across your entire environment. Matano's hundreds of curated out of the box detection rules automatically correlate data to uncover attacker and include coverage for the latest attacks backed by research. Detections are aligned with MITRE ATT&CK® and allow flexible customization to focus on what matters.
Detection engineering
Build advanced detections using a powerful query language integrated across search and detection. Leverage automated enrichment backed by threat intelligence and asset context from the Matano Security Graph. Enable uniform analysis with a common schema (ECS).
Automatic continuous IoC matching
Automate detection using instant correlation of indicators of compromise (IoC) against up to years of security data with continuous and retroactive scanning. Integrated with out-of-the-box intelligence feeds and third-party & custom threat intelligence.
Contextualized alerts in realtime
Matano automatically pulls threat intelligence and asset context into a security graph and combines it with the data lake to deliver high fidelity alerts and help you focus on the threats that matter.
Security Graph
Matano builds an embedded Security Graph of all your assets and resources to power detection and investigation, allowing for user, host, and IP enrichment as well as arbitrary asset context. Leverage deep relational context to prioritize using risk and improve your team’s ability to rapidly respond to incidents.
Use context to power detection
Enrich logs using geolocation, threat intelligence from out-of-the-box and custom feeds, and asset context from the Security Graph. Matano uses context to only escalate relevant threats using risk scoring based on vulnerability and business risk.
Graph powered investigation
Contextualize threats in a single view across your entire security ecosystem and rapidly understand detection impact by correlating it on the Security Graph with relevant network, identity, or other risks in your environment.
Try the Cloud native SIEM built on a security data lake.